Siguiendo las best-practices que Cisco recomienda, en la configuracion de Nexus 7K, y tambien en los Catalyst 6500, se puede configurar una ACL especial llamada CoPP (Control Plane Policy).
Básicamente y de manera gráfica, las CoPP actúan filtrando los paquetes que van directamente a la CPU provenientes del de los planos de control.
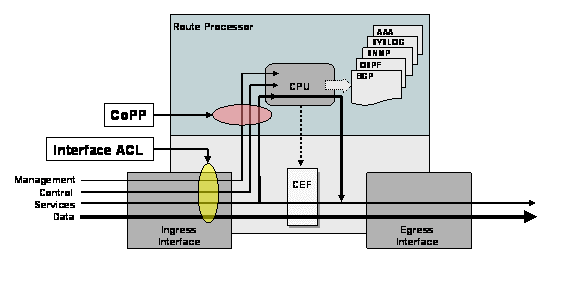
Esta ACL, esta pensada para que en caso de que el equipo reciba mas trafico del que puede procesar, nunca afecte a los procesos internos del router, dejando la sensacion de que el equipo esta "colgado".
Para evitar esto, podemos crear una ACL, basada en politicas de QoS, que protegera el plano de control del equipo, descartando todo el trafico que sobrepase cierto umbral; de esta forma, si hubiera una anomalia en el proceso BGP, por ejemplo, no se "ocuparía" toda la memoria del router (BGP puede consumir ingentes cantidades de la misma), ni saturar ninguna de las interfaces.
A continuación un ejemplo de una CoPP, customizada para un Nexus 7K, para los 6500 es similar con algun cambio en los comandos:
ip access-list copp-system-acl-bgp
10 permit tcp any gt 1024 any eq bgp
20 permit tcp any eq bgp any gt 1024
ipv6 access-list copp-system-acl-bgp6
10 permit tcp any gt 1024 any eq bgp
20 permit tcp any eq bgp any gt 1024
ip access-list copp-system-acl-eigrp
10 permit eigrp any any
ip access-list copp-system-acl-ftp
10 permit tcp any any eq ftp-data
20 permit tcp any any eq ftp
30 permit tcp any eq ftp-data any
40 permit tcp any eq ftp any
ip access-list copp-system-acl-glbp
10 permit udp any eq 3222 224.0.0.0/24 eq 3222
ip access-list copp-system-acl-hsrp
10 permit udp any 224.0.0.0/24 eq 1985
ip access-list copp-system-acl-icmp
10 permit icmp any any echo
20 permit icmp any any echo-reply
ipv6 access-list copp-system-acl-icmp6
10 permit icmp any any echo-request
20 permit icmp any any echo-reply
ip access-list copp-system-acl-igmp
10 permit igmp any 224.0.0.0/24
ip access-list copp-system-acl-msdp
10 permit tcp any gt 1024 any eq 639
20 permit tcp any eq 639 any gt 1024
ip access-list copp-system-acl-ntp
10 permit udp any any eq ntp
20 permit udp any eq ntp any
ipv6 access-list copp-system-acl-ntp6
10 permit udp any any eq ntp
20 permit udp any eq ntp any
ip access-list copp-system-acl-ospf
10 permit ospf any any
ipv6 access-list copp-system-acl-ospf6
10 permit 89 any any
ip access-list copp-system-acl-pim
10 permit pim any 224.0.0.0/24
20 permit udp any any eq pim-auto-rp
ip access-list copp-system-acl-pim-reg
10 permit pim any any
ipv6 access-list copp-system-acl-pim6
10 permit 103 any ff02::d/128
20 permit udp any any eq pim-auto-rp
ip access-list copp-system-acl-radius
10 permit udp any any eq 1812
20 permit udp any any eq 1813
30 permit udp any any eq 1645
40 permit udp any any eq 1646
50 permit udp any eq 1812 any
60 permit udp any eq 1813 any
70 permit udp any eq 1645 any
80 permit udp any eq 1646 any
ipv6 access-list copp-system-acl-radius6
10 permit udp any any eq 1812
20 permit udp any any eq 1813
30 permit udp any any eq 1645
40 permit udp any any eq 1646
50 permit udp any eq 1812 any
60 permit udp any eq 1813 any
70 permit udp any eq 1645 any
80 permit udp any eq 1646 any
ip access-list copp-system-acl-rip
10 permit udp any 224.0.0.0/24 eq rip
ip access-list copp-system-acl-sftp
10 permit tcp any any eq 115
20 permit tcp any eq 115 any
ip access-list copp-system-acl-snmp
10 permit udp any any eq snmp
20 permit udp any any eq snmptrap
ip access-list copp-system-acl-ssh
10 permit tcp any any eq 22
20 permit tcp any eq 22 any
ipv6 access-list copp-system-acl-ssh6
10 permit tcp any any eq 22
20 permit tcp any eq 22 any
ip access-list copp-system-acl-tacacs
10 permit tcp any any eq tacacs
20 permit tcp any eq tacacs any
ipv6 access-list copp-system-acl-tacacs6
10 permit tcp any any eq tacacs
20 permit tcp any eq tacacs any
ip access-list copp-system-acl-telnet
10 permit tcp any any eq telnet
20 permit tcp any any eq 107
30 permit tcp any eq telnet any
40 permit tcp any eq 107 any
ipv6 access-list copp-system-acl-telnet6
10 permit tcp any any eq telnet
20 permit tcp any any eq 107
30 permit tcp any eq telnet any
40 permit tcp any eq 107 any
ip access-list copp-system-acl-tftp
10 permit udp any any eq tftp
20 permit udp any any eq 1758
30 permit udp any eq tftp any
40 permit udp any eq 1758 any
ipv6 access-list copp-system-acl-tftp6
10 permit udp any any eq tftp
20 permit udp any any eq 1758
30 permit udp any eq tftp any
40 permit udp any eq 1758 any
ip access-list copp-system-acl-traceroute
10 permit icmp any any ttl-exceeded
20 permit icmp any any port-unreachable
ip access-list copp-system-acl-undesirable
10 permit udp any any eq 1434
ip access-list copp-system-acl-vrrp
10 permit 112 any 224.0.0.0/24
ip access-list remote_access
10 permit ip any 10.105.20.2/32
20 permit ip any 192.168.0.1/32
!
class-map type control-plane match-any copp-system-class-critical
match access-group name copp-system-acl-bgp
match access-group name copp-system-acl-bgp6
match access-group name copp-system-acl-eigrp
match access-group name copp-system-acl-igmp
match access-group name copp-system-acl-msdp
match access-group name copp-system-acl-ospf
match access-group name copp-system-acl-ospf6
match access-group name copp-system-acl-pim
match access-group name copp-system-acl-pim6
match access-group name copp-system-acl-rip
class-map type control-plane match-any copp-system-class-exception
match exception ip option
match exception ip icmp unreachable
match exception ipv6 option
match exception ipv6 icmp unreachable
class-map type control-plane match-any copp-system-class-important
match access-group name copp-system-acl-glbp
match access-group name copp-system-acl-hsrp
match access-group name copp-system-acl-vrrp
match access-group name copp-system-acl-pim-reg
class-map type control-plane match-any copp-system-class-management
match access-group name copp-system-acl-ftp
match access-group name copp-system-acl-ntp
match access-group name copp-system-acl-ntp6
match access-group name copp-system-acl-radius
match access-group name copp-system-acl-sftp
match access-group name copp-system-acl-snmp
match access-group name copp-system-acl-ssh
match access-group name copp-system-acl-ssh6
match access-group name copp-system-acl-tacacs
match access-group name copp-system-acl-telnet
match access-group name copp-system-acl-tftp
match access-group name copp-system-acl-tftp6
match access-group name copp-system-acl-radius6
match access-group name copp-system-acl-tacacs6
match access-group name copp-system-acl-telnet6
class-map type control-plane match-any copp-system-class-monitoring
match access-group name copp-system-acl-icmp
match access-group name copp-system-acl-icmp6
match access-group name copp-system-acl-traceroute
class-map type control-plane match-any copp-system-class-normal
match protocol arp
class-map type control-plane match-any copp-system-class-redirect
match redirect dhcp-snoop
match redirect arp-inspect
class-map type control-plane match-any copp-system-class-undesirable
match access-group name copp-system-acl-undesirable
!
policy-map type control-plane copp-system-policy
class copp-system-class-critical
police cir 40900 kbps bc 310 ms conform transmit violate drop
class copp-system-class-important
police cir 1060 kbps bc 1250 ms conform transmit violate drop
class copp-system-class-management
police cir 10000 kbps bc 310 ms conform transmit violate drop
class copp-system-class-normal
police cir 680 kbps bc 310 ms conform transmit violate drop
class copp-system-class-redirect
police cir 280 kbps bc 310 ms conform transmit violate drop
class copp-system-class-monitoring
police cir 100 kbps bc 310 ms conform transmit violate drop
class copp-system-class-exception
police cir 360 kbps bc 310 ms conform transmit violate drop
class copp-system-class-undesirable
police cir 32 kbps bc 310 ms conform drop violate drop
class class-default
police cir 100 kbps bc 310 ms conform transmit violate drop
Mas información en...
http://www.cisco.com/en/US/docs/switches/datacenter/sw/4_1/nx-os/security/configuration/guide/sec_cppolicing.html
